Duo Security Integration Overview
This document describes how to integrate WatchGuard Mobile VPN with SSL client software download access and Mobile VPN with SSL client authentication with the Duo Security® two-factor authentication solution.
You must install a local Duo Proxy service on a device within your network. The Duo Proxy receives incoming LDAP requests from your Firebox, contacts your existing local LDAP/AD server to perform primary authentication, and contacts the Duo cloud service for secondary authentication.
Test Topology
This diagram shows the test topology for this integration.

Platform and Software
The hardware and software used in this guide include:
- Firebox with Fireware v12.8 or higher
- Duo Security Authentication Proxy 5.6.1 on Windows
- Windows Server 2016 with Active Directory Domain Services
- Duo Mobile Application 4.15.0.43.1 on iOS
Configuration
To complete this integration, you must have:
- Duo account
- Duo Security Authentication Proxy
- Active Directory
- WatchGuard Firebox
Use the Duo account to log in to the Duo Service to manage applications, enroll users, and get integration keys. The Duo Authentication Proxy acts as a bridge: it communicates with Active Directory, Duo Security service in the cloud, WatchGuard Firebox, and Duo mobile app. Active Directory is used for primary user authentication.
In our configuration, Duo Security Authentication Proxy and Active Directory are located on the same subnet.
Configure Firebox
You must configure the LDAP authentication settings and enable Mobile VPN with SSL on your Firebox.
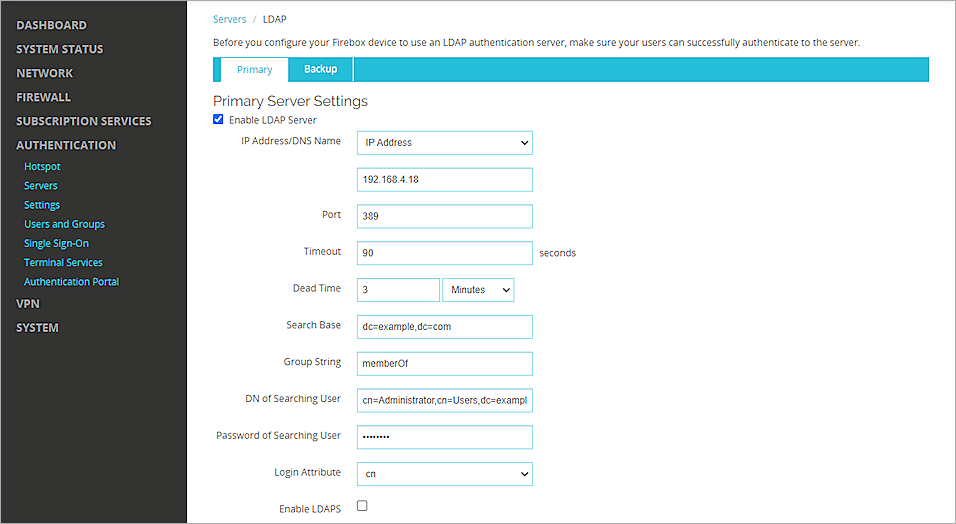
Configure LDAP Authentication
- Log in to Fireware Web UI (https://<your firebox IP address>:8080).
- Select Authentication > Servers.
The Authentication Servers page appears. - From the Authentication Servers list, select LDAP.
The LDAP page appears. - Select the Enable LDAP Server check box.
- From the IP Address/DNS Name drop-down list, select IP Address.
- In the text box adjacent to IP Address/DNS Name, type the Duo Security Authentication Proxy IP address.
- In the Port text box, type 389.
- In the Timeout text box, type 90.
- In the Search Base text box, type the search base settings in standard format: dc=first part of distinguished server name, dc=any part of the distinguished server name that appears after the dot.
- In the DN of Searching User text box, type the distinguished name (DN) for a search operation.
For example: cn=Administrator,cn=Users,dc=example,dc=com. - In the Password of Searching User text box, type the password associated with the distinguished name for a search operation.
- From the Login Attribute drop-down list, select an LDAP login attribute to use for authentication. In our example, we select cn. In some cases, you might need to select other values, such as sAMAccountName.
- Keep all other settings as the default values.
- Click Save.

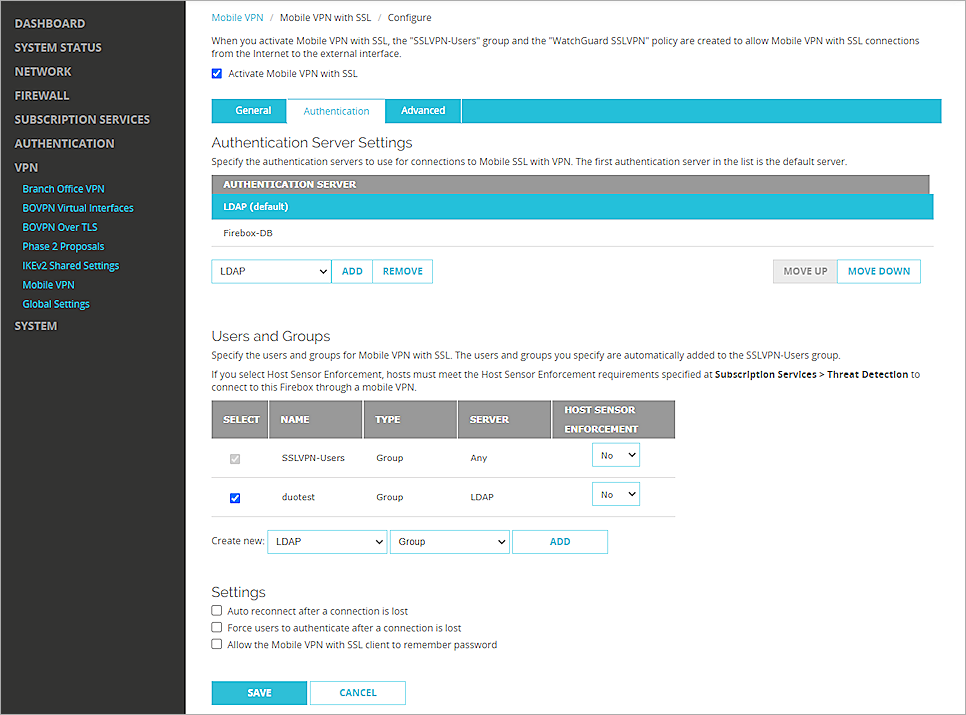
Configure Mobile VPN with SSL
From Fireware Web UI:
- Select VPN > Mobile VPN.
- In the SSL section, click Manually Configure.
- Select the Activate Mobile VPN with SSL check box.
- In the General section, for the Primary text box, type the public IP address (external IP address) or domain name of the Firebox. This is the IP address or domain name that mobile VPN with SSL clients connect to by default.
- Select the Authentication tab.
- From the Authentication Server drop-down list, select the authentication server you created.
- Click Add.
- In the Authentication Server list, select your authentication server and click Move Up to move it to the top of the list (this makes it the default authentication server).
Mobile VPN with SSL uses the default authentication server unless a user specifies an authentication server in the Username text box on the Mobile VPN with SSL client. - In the Users and Groups section, from the Create new drop-down list, select the authentication server you created.
- From the adjacent drop-down list, select Group. You can add a user or a group. In our example, we add a group.
- Click Add.
The Add User or Group dialog box appears. - For Type, select Group.
- In the Name text box, type a name for the group. The name of this group must be the same as the name of the Active Directory group your users belong to.
- From the Authentication Server drop-down list, select your authentication server.
- Click Save.
- Click Save.

Configure Duo
Set Up an Application
- Sign up for a Duo account.
- Log in to the Duo Admin Panel and select Applications.
- Select Protect an Application and find LDAP Proxy in the application list.
- Select Protect to get the values of the Integration key, Secret key, and API hostname.
- Click Save.
Sync Users to Duo from Active Directory
Organizations with an existing on-premises Microsoft Active Directory domain can import users, phones, and groups into Duo with directory synchronization.
For detailed instructions about how to sync users from Active Directory, see Synchronizing Users from Active Directory.
Configure the Duo Security Authentication Proxy for Primary Authentication
The Duo Security Authentication Proxy validates the user password. In our integration, you must configure the Proxy to communicate with the Active Directory.
To configure the Proxy, add an [ad_client] section at the beginning of the file that includes the properties described in this list. All properties are required.
|
Properties |
Description |
|---|---|
| host |
The hostname or IP address of your domain controller. |
|
service_account_username |
The user name of a domain account that has permission to bind to your directory and perform searches. |
| service_account_password |
The password corresponds to service_account_username. |
|
search_dn |
The LDAP distinguished name (DN) of an Active Directory container or organizational unit (OU) contains all of the users you want to permit to log in. |
For example:
[ad_client]
host=192.168.4.19
service_account_username=Administrator
service_account_password=Passw0rd
search_dn=DC=example,DC=com
Configure the Duo Security Authentication Proxy to Work with the Firebox
To configure the Duo Authentication Proxy to work with the Firebox, create a [ldap_server_auto] section in the Proxy configuration file that includes the properties described in this list. All properties are required.
Save the configuration file when you are done.
|
Properties |
Description |
|---|---|
| ikey |
The Integration key, as referenced in the Setting Up an Application section of this document. |
| skey |
The Secret key, as referenced in the Setting up An Application section of this document. |
| api_host |
The API hostname, as referenced in the Setting up An Application section of this document. |
|
client |
Set this value to ad_client so that the Proxy uses Active Directory/LDAP for primary authentication. Make sure an [ad_client] section as described previously is configured. |
An example configuration file that uses Active Directory as the primary authenticator:
[ad_client]
host=192.168.4.19
service_account_username=Administrator
service_account_password=Passw0rd
search_dn=DC=example,DC=com
[ldap_server_auto]
ikey=DI4D2NIDOJK13LO57WA0
skey=jqKSHXxFqimTOv6DUZ7xwY2Qm164B2XNtwiNE6mv
api_host=api-537a49ce.duosecurity.com
client=ad_client
failmode=safe
exempt_primary_bind=false
exempt_ou_1=cn=Administrator,cn=Users,dc=example,dc=com
Start the Duo Authentication Proxy
On the Windows computer where the Duo Authentication Proxy is installed, open an Administrator command prompt and type this command:
net start DuoAuthProxy
Test the Integration
To test the integration of your Mobile VPN with SSL, authenticate with a mobile token on your mobile device. You can authenticate with a passcode or a push notification.
If you select passcode authentication, you must type the password followed by a comma and append the passcode from the Duo Mobile App.
In this example, we show the push authentication method (users receive a push notification in the mobile app that they must approve to authenticate).
- Open your Mobile VPN with SSL client.
- In the Server text box, type the external IP address of the Firebox.
- In the User name text box, type the user cn value.
- In the Password text box, type the password.
- Click Connect.
- Approve the authentication request that is sent to your mobile device.
The VPN connects successfully.
